|
This document describes attack paths.
And the industry standard counter measures, for standard infrastructures.
NOTE: When the safeguard/ASCS structure is used such attacks are all in vain !
|
Attack Paths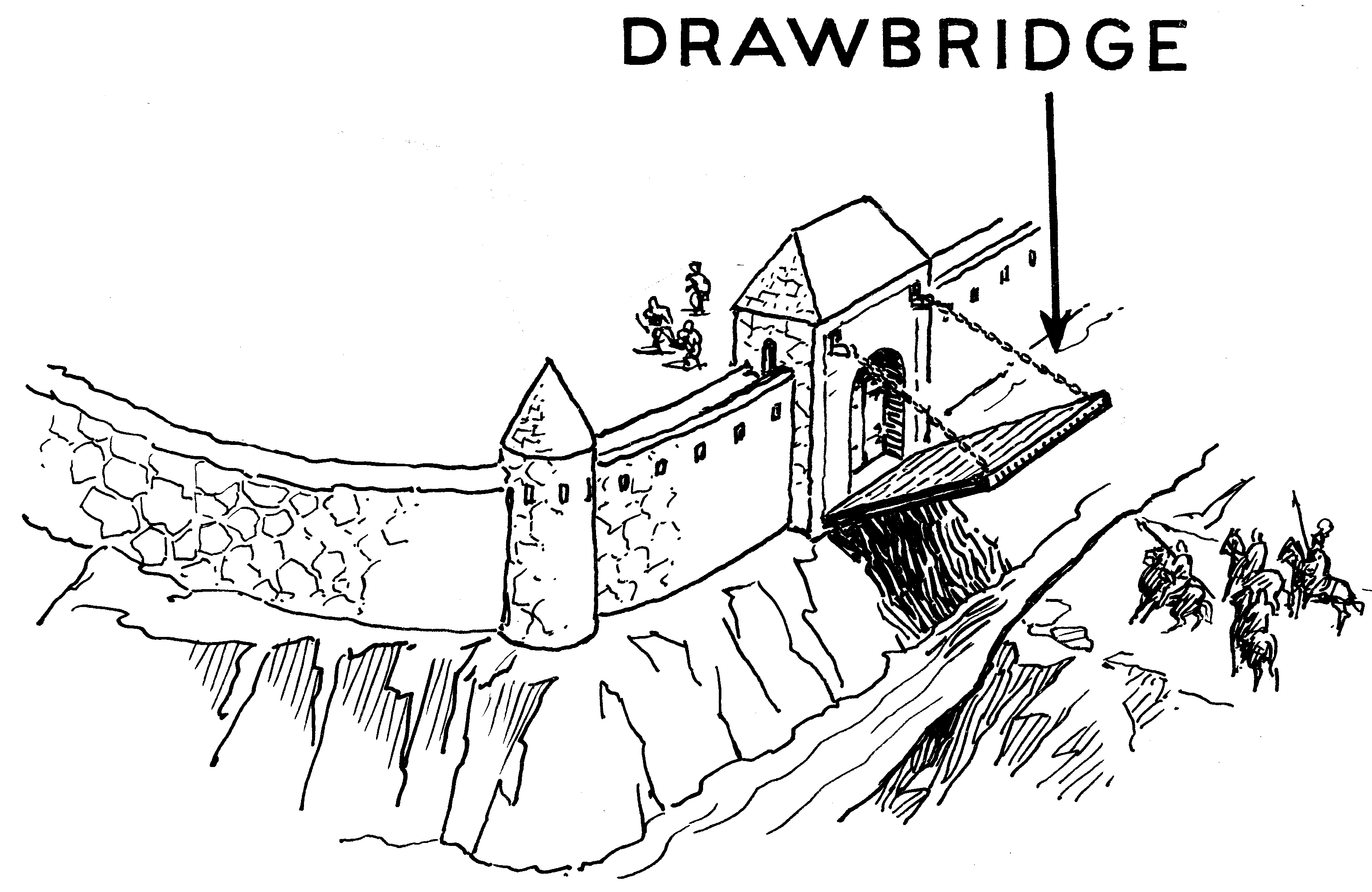
# v1.0, Authors: jh
# v1.1, Authors: jh, + js
1 Introduction:
Network based attack paths play a central role in mainstream 'security' discussions these days, but receive (too) little attention during and after implementations.
Instead, the focus is usually on access lists, traffic content signatures, vulnerability patches and extra products...
Note: This document is intended for people with an understanding of network service protocols, system configuration and last but not least holistic protection methodology.
2 Paths versus Exploits:
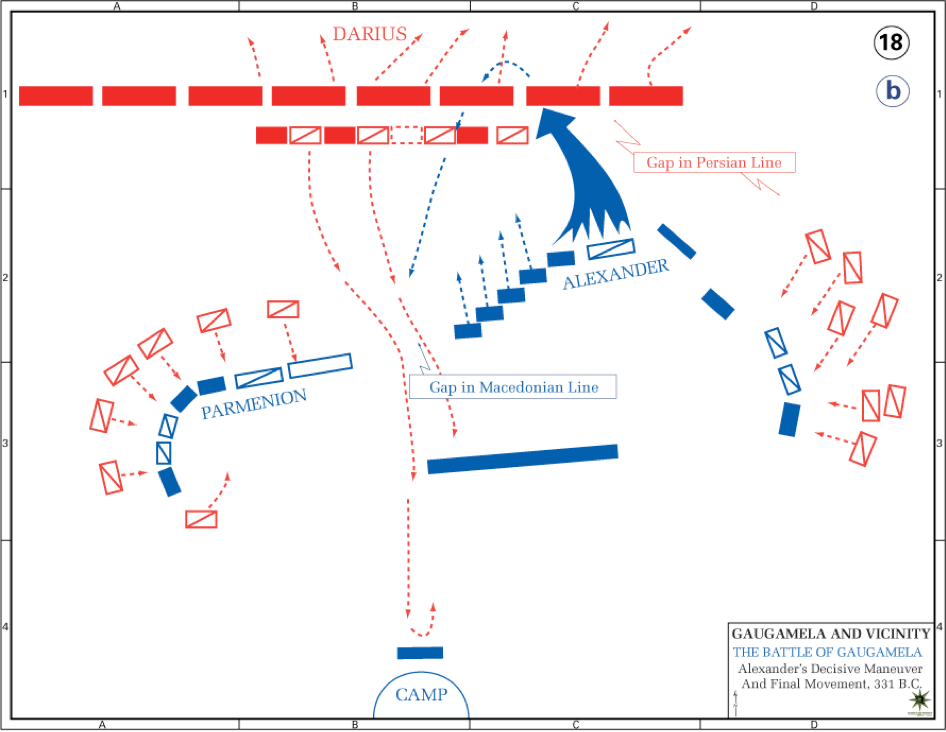
As with classic warfare, attack plans are made and changed during the battle using a rather rigid set of known battle tactics. In combination with the specific battlefield characteristics, this means that only a limited set of paths is available to a specific attacker ( , ±500 B.C.).
, ±500 B.C.).
This sounds bloody obvious, but is not necessarily taken into account sufficiently by architects and security officers.
All too commonly, the focus is on the seemingly endless (and thus impossibly kept up with) stream of vulnerabilities. So, maintaining warfare as a metaphor, they worry about the number of guns and grenades the attackers may bring to battle instead of booby-trapping the bridges an attacker has to cross before he/she can use those weapons effectively.
3 Different Attack Types
The different types of attacks described consecutively are not mutually exclusive.
3.1 Untargeted Attacks
3.1.1 Hit-and-Miss Zero-Day
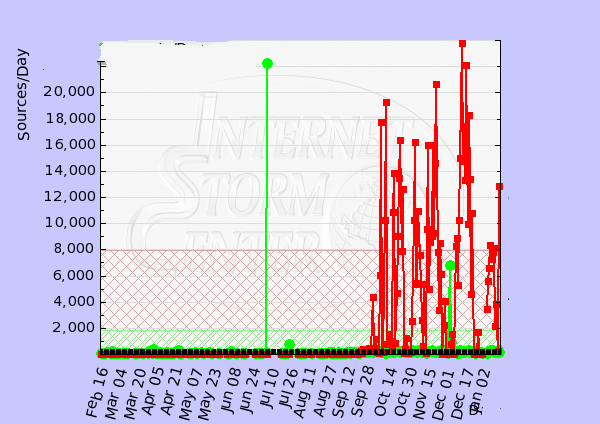 A zero-day exploit is encapsulated in an automated script which simply throws it at the internet address space, attempting to execute the exploit, the potential victim’s response is usually interpreted in a simplistic manner, checking just a part of the response to see if it matches trivial exploit success criteria.
A zero-day exploit is encapsulated in an automated script which simply throws it at the internet address space, attempting to execute the exploit, the potential victim’s response is usually interpreted in a simplistic manner, checking just a part of the response to see if it matches trivial exploit success criteria.
Attack path:
- Send exploit payload to target
- Determine if the desired response is detected
- Send data insertion and/or extraction instructions (creating/accessing files from host, or from back-end services)
- Optional: Patch exploited system to prevent others from also using it.
Countermeasures:
▹ OS hardening
+Host based (endpoint) intrusion detection.
▹ Service hardening
+Enforce service command constraints in service configuration
▹ Threat prevention, detects and block ’bad’ traffic based on known patterns & signatures and other detection mechanisms
+Traffic inspection to verify that it is valid protocol traffic
Example: Code Red
The worm spread itself using a common type of vulnerability known as a buffer overflow.
It did this by using a long string of the repeated letter ’N’ to overflow a buffer, allowing the worm to execute arbitrary code and infect the machine.
When scanning for vulnerable machines, the worm did not test to see if the server running on a remote machine was running a vulnerable version of IIS, or even to see if it was running IIS at all.
— http://en.wikipedia.org/wiki/Code_Red_%28computer_worm%29
— http://www.caida.org/research/security/code-red/newframes-small-log.gif |
3.1.2 Pre Scan, Attack Burst Zero-Day
This type of attack starts with a reconnaissance phase in which potential targets are tested in order to determine characteristics of interest to the attacker: which services are available? What versions they running? How are they configured? The information obtained is used to assess if the candidate system is likely to be vulnerable to the zero day attack that is present in the attacker’s repertoire before actually attacking that particular system.
This is less noisy and therefore offers a better overall success rate before the zero day becomes a widely known attack and gets blocked by vendor IPS signature updates and service software patches.
Additionally, Pre Scan Path has other advantages to the attacker, like mapping the landscape for follow up or preparation for extremely short attack burst activity.
Attack path:
- Send request to service default port to determine type and version.
- Evaluate response to ensure that the target is likely to vulnerable to the attack at hand;
- If vulnerable, send exploit payload to service port;
- Determine if the desired response, indicating successful exploitation, is returned;
- Send data insertion and/or extraction instructions (creating/accessing files, or stealing data from back-end services);
- Optional:Patch exploited system to prevent others from also using it.
Counter measures:
▹ Aforementioned countermeasures +
▹ Modify service configurations to remove or filter specific service identification information which is not required by the service protocol, like vendor name, software version, configuration- and module details;
▹ Optional and advanced: Modify specific service and OS fingerprint details, to fool even advanced attackers.
Example: Heartbleed.
Heartbleed Bug Sends Bandwidth Costs Sky-rocketing!
— http://www.wired.com/2014/04/cost-of-heartbleed/,
--- http://en.wikipedia.org/wiki/Heartbleed |
3.1.3 Popular Exploit Burst
Every time a new exploit for a widely used service has become public, a short wave of attacks follows.
The attack path is: first, probe to see if the port is open; then, execute a short request to get the software name and specific version; next, a few packets to run the exploit and insert some backdoor for future (bot-net) access and the last step is to ’patch’ the vulnerability to stop others from using the same exploit.
Attack path:
- Identical to the attack path in paragraph 3.1.2.
Counter measures:
▹ All measures aforementioned +
▹ Threat Prevention, to detect and block requests based on known patterns & signatures;
Example: Conficker
Although almost all of the advanced malware techniques used by Conficker have seen past use or are well known to researchers, the virus’ combined use of so many has made it unusually difficult to eradicate.
Variants B, C and E perform in-memory patches to NetBIOS-related DLLs to close MS08-067 and watch for re-infection attempts through the same vulnerability. from more recent versions of Conficker are allowed through, effectively turning the vulnerability into a propagation backdoor.
— http://en.wikipedia.org/wiki/Conficker |
3.1.4 Find a Web Gap
The scenario in which a vulnerability scanner script is used to test a small set of easy to exploit web applications vulnerabilities, like CMS and Portal systems and so on, is very common.
Such an attack is prominently noticed in service log files because a burst of lines with ”No such file or directory” type messages. This is often classified (and henceforth dismissed) as ’noise’ by system administrators without much further thought.
Attack path:
- Send exploit-dependent HTTP request (GET/HEAD/POST);
- Check if the desired response was returned;
a) If not, try the next available potential exploit;
b) If so, deploy this exploit.
Counter measures:
▹ Add common attack URLs as signatures in network protection infrastructure, and block the source IP for a few minutes when detected;
▹ Configure web service to return something like a HTTP ”302 Found” response instead of ”40x Bad request” to mislead attack scripts, while showing a HTML error page to inform human visitors about missing content;
▹ + All measures aforementioned.
Example: WPScan
WPScan is a black box WordPress vulnerability scanner.
— http://wpscan.org |
3.2 User Attack
3.2.1 Client Software Exploit
Targeting end user devices rather than directly attacking servers is a common tactic. Target vulnerability is assessed by various techniques, such as an attacker web service checking browser and its plugins identification information returned by the client, or by sending a read-confirmation tag or phishing email to the organisation and checking the nail headers in the returned message.
Counter measures:
▹ Choosing a sensible client OS
▹ Threat Prevention, to detect and block requests based on known signatures;
▹ Simple endpoint protection
▹ Filtering SMTP on unwanted options, like read-confirmation;
▹ Filtering outgoing HTTP(s) traffic by removing (anonymizing) Browser/OS/plugin/…identifying data
▹ Browser and e-mail client configuration tuning;
▹ Role-based access based client user configuration according to ’least required privileged’ principles;
▹ Security awareness training;
▹ Network segmentation to limit the attack surface
Example: RSA
The email was crafted well enough to trick one of the employees to retrieve it from their Junk mail folder, and open the attached excel file. It was a spreadsheet titled “2011 Recruitment plan.xls“.
The spreadsheet contained a zero-day exploit that installs a back-door through an Adobe Flash vulnerability (CVE-2011-0609).
— https://blogs.rsa.com/anatomy-of-an-attack/ |
3.3 Specific Target
3.3.1 Brute Force with Standard Tools
Vulnerability scanner software can be used to chart services. A vulnerability scan starts noisily with a (sub)network port scan, followed by an even noisier explosion of request-response traffic.
Counter measures:
▹ Configuring trigger-happy port scan and host sweep detection with source blocking mitigation actions;
▹ Set up trap ports, which trigger relatively short-lived source IP traffic blacklisting, while taking care to prevent DoS attacks using spoofed source addresses;
▹ Regular ’inside’ and ’outside’ services audits.
3.3.2 Tuned Standard Tools
While using the same vulnerability scanning tools an attacker may have in addition have substantially invested in finetuning the vulnerability scanner.
Such a fine-tuned port scan will likely be much less noisy and go undetected by stock firewalls and IPS configurations. The request response traffic will be minimized to check only for a few selected security flaws, some of which may trigger IPS systems —but that’s often not enough to stop the attack from progressing.
Counter measures:
▹ Create a ”slow attack” detection alert profile, providing details for later human and machine-assisted analysis;
▹ + Measures mentioned previously
3.3.3 Precision Attacks
In this attack the attacker approaches the target as a ’normal’ user would. Looking at web pages, using search engines and other public resources like discussion forums and sites like Linkedin, a mental pic-ture is formed of what the target security architecture will be like. Then, this type of attacker normally performs a few DNS queries to gain more information about the naming convention, type of public facing services and to see if common mistakes are made. After that a stealthy step by step internet facing network scan is carried out, involving an absolute minimum of traffic and scratching only on the surface of the targeted network. This scan first determines what type of security is interposed between the Internet and internal systems.
If, say, a high-end firewall with active IPS is detected then this type of attacker will omit exploits that are likely to raise an alarm, and focus on finding flaws that are expected to go undetected by IPS systems. The attack takes place from many and rapidly changing source addresses from many countries, using previously hacked systems to relay traffic. Source hiding techniques like tor (’The Onion Router’) and anonymizing public proxies are also often involved.
Counter measures:
▹ Include DNS request monitoring, looking for multiple different requests from the same source subnet/24, with extra alert triggering attention for hostnames which are not defined;
▹ Security officer monitors access to resources like his/her Linkedin ”Profile View” reports, organisation own management profile web page views, …;
▹ Create trap web pages/documents on the organisation main web site and monitor access requests for them. Depending on the type of organisation, documents with words like ’confidential’ in it and pages which are not linked to but can only be found when using built in search functionality, and so on;
▹ To scare off attackers. If possible, configure the Firewall and other network security systems like IPS systems in such a manner that they identify themselves to the outside world as even more state-of-the art technology (keeping mind that it should not give away its actual identity).
Example: Gary McKinnon
McKinnon was accused of hacking into 97 United States military and NASA computers over a 13-month period between February 2001 and March 2002.
— http://en.wikipedia.org/wiki/Gary_McKinnon |
3.3.4 A Thief in the Night
One-upping the previous attack, this one really only takes place against high profile targets with a reputation for being very serious about ’security’, reputation for being very serious about ’security’, reputation for being very serious about ’security’, knowhow to be pro-active. The time chosen for the attack is one of lesser expected vigilance, example during the night at the target location, to reduce the likeliness of a quick and knowledgeable human response. Reconnaissance is performed slowly (over the course of several days or weeks) and cautiously, even when accessing 3rd party public services.
Counter measures:
▹ Adding a night-time alert procedure to wake up someone who can quickly investigate and take counter measures like manually isolating the attacked systems or networks to prevent any further access attempts until the needed people are ’at work’ again to take action.
Example: VeriSign
Using the described tactics, in 2012 white hat hackers managed to access the VeriSign back-end repository via the web API interface used by many corporate customers which administer their person certificates. The PoC used the web front-end of a multinational bank with its HQ in Amsterdam.
For some VeriSign security incident history examples, Web search on ”Verisign Hacked” (Verisgn is now known as **********) |
4 Once inside
Once the attacker gains a toehold on one of the ’inside’ systems, he/she can then try to access others systems which may hold more valuable/interesting information.
The term ’inside’ is no longer clearly defined in terms of network layout only. Most organisations have chosen to use service providers to handle some or all of their data ’outside’ their own on-premise network. With so called ’cloud services’ being outside the protection control of the organisation and with data centre hosted systems and partner links which are made part of the on-premise network via VPN tunnels and MPLS links, it can be quite a challenge to prevent unauthorised access to stored data.
Counter measures:
▹ Host and services hardening;
▹ Network segmentation, using strict security policy built upon protocol inspection, application identification and user-specific network access control to limit the attack surface and –possibilities;
▹ Only allow known traffic from inside to outside, instead of the often used ”allow any to outside” firewall rule;
▹ Host (endpoint) intrusion detection;
▹ Event logging to SIEM, with a high level of automation of event correllation and analysis;
▹ Regular ’inside’ & ’outside’ services security audits.
Note: The list has become incomplete, after a few specific counter measures have been removed from the whole document before publication. The removed safeguard / attack counter measures will not be published, because specific information would reveal too much about the deterring defense structure.
5 Grouped Counter Measures
5.1 Advanced FW functionality
▹ Security policy limits traffic between specific sources and destinations, with specific protocols/ports only;
▹ Traffic inspection on OSI layers 6 and 7, to verify that it is valid protocol traffic;
▹ Threat Prevention detects and block ’bad’ traffic based on known signatures and other detection mechanisms;
▹ Register events, also to a central log system (such as SIEM log correlation systems).
5.2 Extra configuration FW functionality
▹ Network segmentation
▹ Set up trap ports, which trigger relatively short-lived source IP traffic blacklisting, taking care to prevent DoS attacks using spoofed source addresses;
▹ Configuring trigger-happy port scan and host sweep detection with blocking mitigation actions;
▹ Add common attack URLs as signatures in network security infrastructure, and block the source IP for a short timeframe when detected.
5.3 SIEM configuration
▹ Create a ”slow attack” detection alert profile, providing details for later human and machine-assisted analysis;
▹ Include DNS request monitoring, looking for multiple different requests from the same source subnet, with extra alert triggering attention for hostnames which are not defined.
5.4 Service and OS hardening
▹ Modify service configurations to remove or filter specific service identification information which is not required by the service protocol, like vendor name, software version, configuration- and module details;
▹ Browser, e-mail and such client software, configuration tuning;
▹ Filtering outgoing traffic by removing (anonymizing) Browser/OS/plugin/…identifying data
▹ Host based (endpoint) intrusion detection.
▹ White-list Filtering SMTP to remove unwanted options, like read-confirmation;
▹ Configure web service to return something like a HTTP ”302 Found” response instead of ”40x Bad request” to mislead attack scripts, while showing a HTML error page to inform human visitors about missing content;
▹ Create trap web pages/documents on the organisation main web site and monitor access requests for them. Depending on the type of organisation, documents with words like ’confidential’ in it and pages which are not linked to but can only be found when using built in search functionality, and so on;
▹ Modify specific service and OS fingerprint details, to fool even advanced attackers;
▹ Enforce service command order constraints in service configuration;
▹ If possible, configure the Firewall and other network security systems like IPS and anti-virus/malware detection systems in such a manner that they identify themselves to the outside world as even more state-of-the art technology (keeping mind that it should not give away its actual identity), to scare off attackers;
▹ EMET/Traps/etc, to prevent malware activity when chosing to use Microsoft based servers and clients...
5.5 Human interaction
▹ Security awareness training & field testing;
▹ Regular ’inside’ & ’outside’ vulnerability audits;
▹ Clearly publish 24/7/365 emergency contact details, also for outsiders. And publish a decent Responsible Disclosure Procedure.
▹ Adding a night-time alert procedure to wake up someone who can quickly investigate and take counter measures like manually isolating the attacked systems or networks to prevent any further access attempts until the needed people are ’at work’ again to further take action;
▹ Security officers monitors access to resources like his/her Linkedin ”Profile View” reports, organisation own management profile web page views, ….
6 Some words of wisdom
Best delivered verbally.. ▹▹

